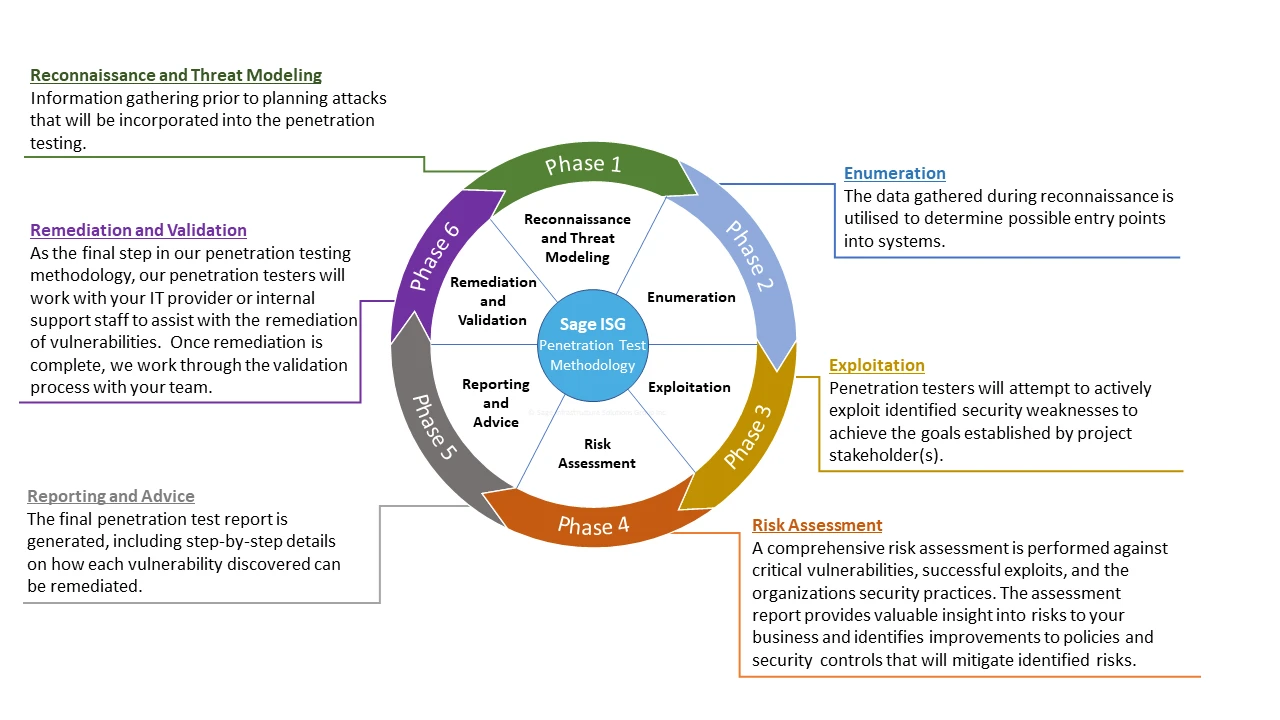
Penetration Testing
Employ cutting-edge techniques to simulate genuine cyber-attacks
Our seasoned team of ethical hackers, based in Calgary, Alberta, employs cutting-edge techniques to simulate genuine cyber-attacks. We identify and address vulnerabilities in your security controls, ensuring the long-term protection of your valuable digital assets. Choose from our diverse range of penetration testing options, including White Box, Grey Box, and Black Box testing, to find the perfect solution for your organization's unique requirements.
By understanding the unique advantages and outcomes of each penetration testing approach, you can make an informed decision on the best course of action for your organization. This knowledge will enable you to prioritize security measures that have the most significant impact on safeguarding your valuable assets, ensuring the continued success and growth of your business.
- Reduce risk by uncovering and addressing security vulnerabilities.
- Ensure compliance with industry standards and regulations, such as PCI-DSS, HIPAA, and Meritas.
- Save on potential costs associated with cyber-attacks, data breaches, and reputational damage.
- Strengthen your organization's overall security posture.
- Monitor and respond to emerging threats proactively.

Providing outcome focused services that will help your organization achieve its security goals
As a Canadian business, we appreciate the significance of protecting your data, reputation, customer trust, and we are committed to providing outcome focused services that will help your organization achieve its security goals. At the end of every engagement, our team will provide a detailed report that outlines clear, actionable insights.
Utilizing advanced tools and technologies, our comprehensive penetration testing services identify vulnerabilities that may otherwise slip under the radar. Additionally, we offer ongoing support and regular vulnerability assessments to ensure your security remains robust over time.
Choose Sage Infrastructure Solutions Group to safeguard your organization's future.
White Box Testing
White Box testing is an in-depth evaluation of your organization's internal systems, networks, and applications.
- A thorough understanding of your organization's security architecture, pinpointing weak points and potential attack vectors.
- Identification of security vulnerabilities originating from design flaws, coding errors, misconfigurations, and other internal issues.
- Comprehensive recommendations for addressing identified vulnerabilities, prioritizing those that pose the most significant risk, and suggesting improvements in development processes and security policies.
- Enhanced protection of sensitive data and intellectual property by reinforcing security measures on both the application and infrastructure levels.
- Early detection of security issues, enabling your organization to address them before they can be exploited by malicious actors.
Grey Box Testing
Grey Box testing supplies a balanced approach to penetration testing by granting our ethical hacker’s partial access to your organization's system information and documentation.
- A practical perspective on the security of your systems, networks, and applications, offering insights into vulnerabilities that may be exploited by an attacker with limited knowledge of your organization's infrastructure.
- Uncovering security gaps that could be leveraged by cybercriminals, including weaknesses in access controls, authentication mechanisms, and encryption protocols.
- Actionable insights for enhancing security measures based on realistic threat scenarios, helping your organization stay one step ahead of potential attackers.
- Improved detection and prevention of insider threats by evaluating your organization's security posture from an attacker's viewpoint.
- Identification of opportunities to optimize security monitoring, incident response, and user awareness training programs.
Black Box Testing
Black Box testing, also known as blind testing, simulates real-world cyber-attacks by providing our ethical hackers with no prior knowledge of your organization's systems or networks.
- Insights into the security vulnerabilities that are most susceptible to external threats, helping your organization prioritize resources and efforts to protect its most critical assets.
- An evaluation of your organization's defences from an outsider's perspective, revealing potential blind spots and areas of improvement.
- Recommendations for strengthening your security posture against real-world cyber-attacks, focusing on perimeter defences, intrusion detection and prevention systems, and security awareness training for employees.
- Assessment of your organization's resilience to cyber-attacks, highlighting the effectiveness of existing security measures and identifying areas where additional safeguards may be needed.
